Incident Response Plan
Incident Response Plan Overview
Purpose
This document provides a brief overview of the Incident Response Plan and offers guidance for employees or incident responders who believe they have discovered or are responding to a security incident.
Scope
The Incident Response Plan applies to all parties that access AC Transit information (e.g., employees, contractors, third-party, and Managed Service Providers). This plan covers all information systems, applications, and data owned, operated, or managed by AC Transit.
Incident Response Process
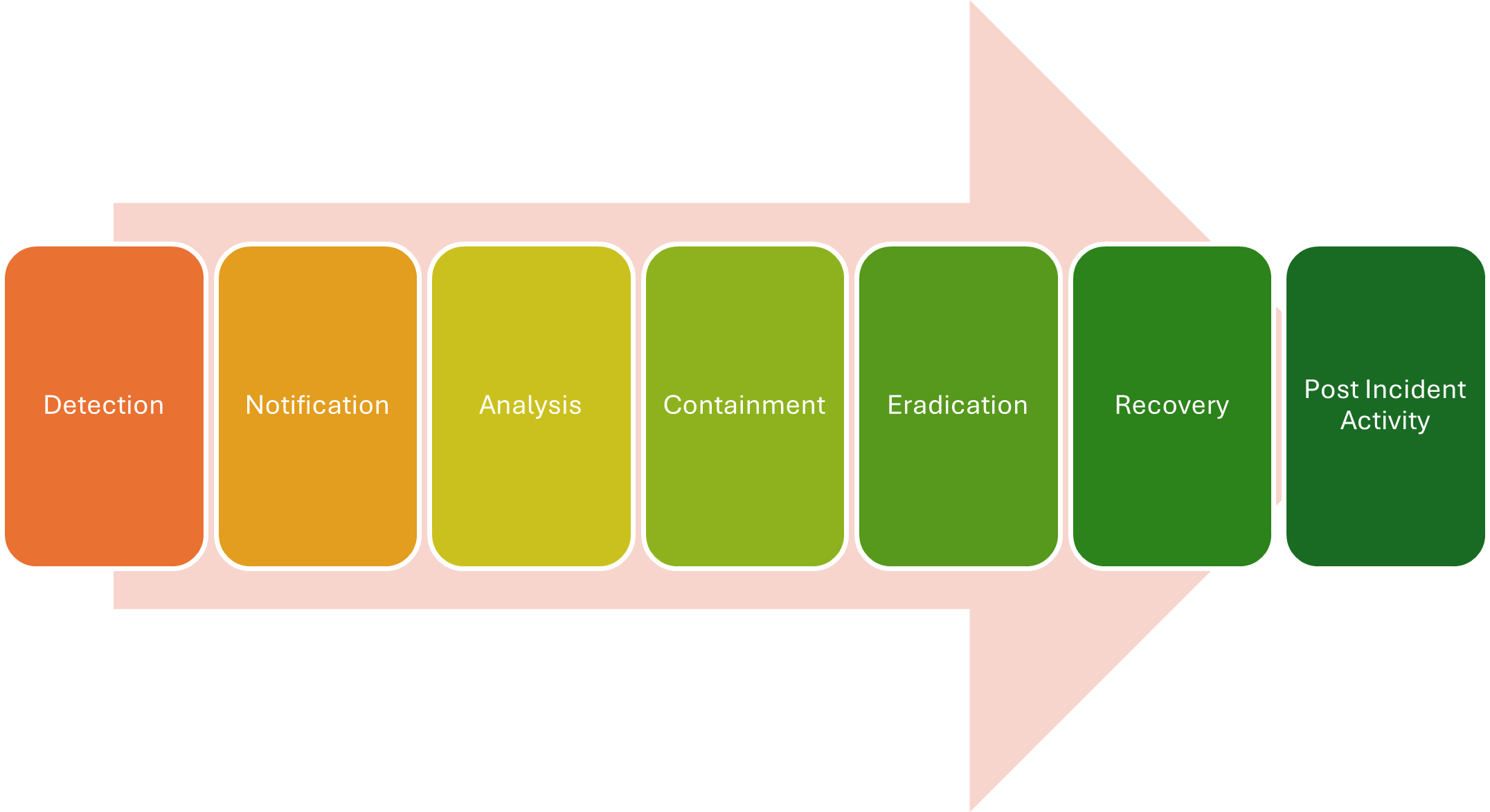
AC Transit executes the Incident Response Plan within the seven phases of Incident Response: Detection, Notification, Analysis, Containment, Eradication, Recovery, and Post Incident Activity.
Incident Reporting & Documentation
Reporting
- Upon discovering an issue (e.g., vulnerability/threat), contact AC Transit:
- Insert Contact Form
Reports should include specific details about what has been observed or discovered.
Documentation
All reported security events, incidents, and response activities shall be logged, assigned a severity level (low/medium, high, or critical), backed up, and saved.
Severity
Low
- Issues meeting this severity have a minor impact on a small portion of the enterprise.
- Action Timeline: Within 24 hours
Medium
- Issues meeting this severity have some impact on a small portion of the enterprise.
- Action Timeline: Within 4 hours
High
- Issues meeting this severity involve the loss of a major service within the enterprise.
- Action Timeline: Immediately
Severe
- Issues meeting this severity have an extreme impact on the enterprise.
- Action Timeline: Immediately
Incident Response Process
For critical issues, the response team will follow a rigorous response process designed to investigate, contain exploitation, eradicate the threat, recover system and services, remediate vulnerabilities, and document a post-incident review, cataloging the lessons learned to avoid similar issues in the future.
Summary
- Event reported
- Triage and analysis
- Investigation
- Containment & neutralization (short term work)
- Recovery & vulnerability remediation
- Hardening & Detection improvements (lessons learned, long term work)
- promptly and properly notify customers, partners, users, affected parties, and regulatory agencies of relevant incidents or breaches in accordance with AC Transit policies, contractual commitments, and regulatory requirements.
Roles & Responsibilities
Every employee and user of any AC Transit information resources has responsibilities toward the protection of the information assets. The table below establishes the specific teams included in the Incident Response Team:
| Chief Information Officer | Chief Information Security Officer |
| Vice President of Human Resources | Affected system or operations representative(s) |
| Legal Counsel | Marketing |
| Senior Management (General Manager) | Public Relations |
| Chief Financial Officer (CFO) | IT Manager |
| Chief Operations Officer (COO) | Call Center/Operations Control Center operations |
| Internal Investigator(s) | Any other person(s)/entity deemed appropriate |
Management Commitment
AC Transit management is committed to providing the resources, tools and training needed to reasonably respond to identified security events and incidents with the potential to adversely affect the company and/or its customers.
Violations & Enforcement
Any known violations of this policy should be reported to the IT Manager. Violations of this policy may result in immediate withdrawal or suspension of system and network privileges and/or disciplinary action in accordance with company procedures up to and including termination of employment.
Version
| Version | Description | Date | Author | Approved By |
| 1.0 | First Version | 2/15/2024 | IT Department | CIO |